5 Best VPNs for Cybersecurity
Why Use VPNs?
A virtual private network (VPN) offers an additional layer of anonymity, permits access to foreign websites, and provides safe connections for the transmission of critical business data. While VPNs are primarily used by Individuals, they also provide organizations with the ability to manage numerous user identities, restrict certain sorts of material, and protect sensitive information from hackers.
Casual surfing, online shopping, circumventing geo-restricted material, or torrenting – any online activity is exposed to your ISP or malicious actors if you are not connected to a VPN.
Benefits of Using VPNs
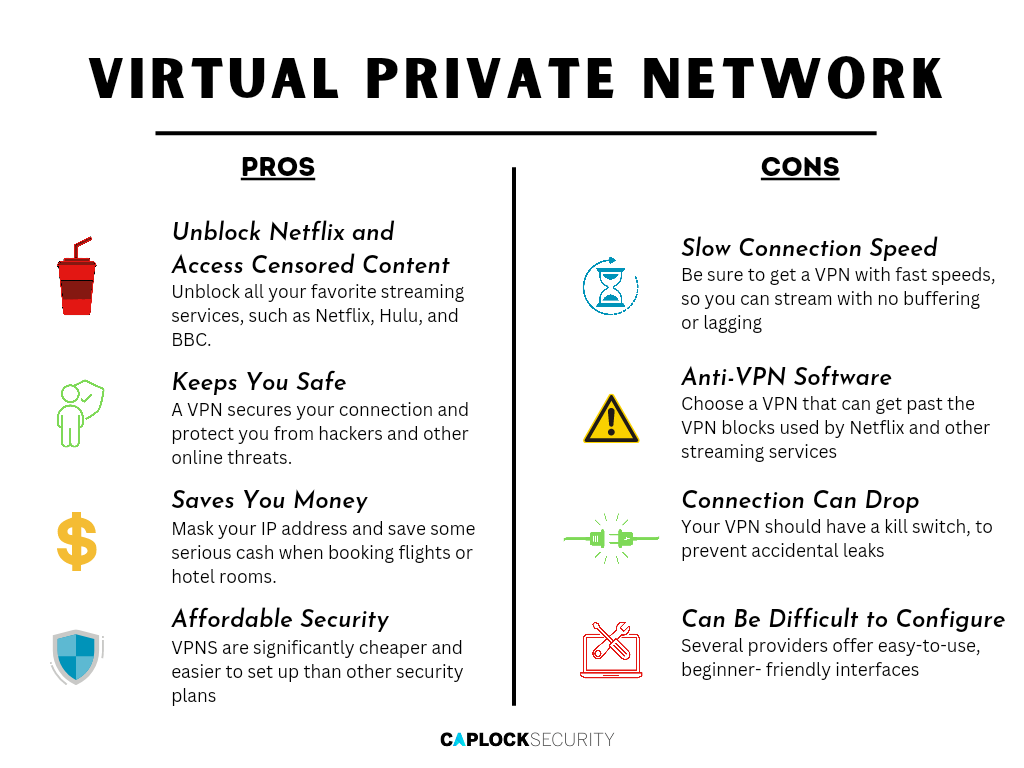
- Hide your private information from the applications and services you use (email, search engine plugins)
- Guaranteed risk-free connection to the network of your firm
- Customers will always have the reassurance that they are safe while using VPNs
- Virtual private networks (VPNs) considerably cut down on both online threats and security breaches
- Enables you to visit websites that are prohibited regardless of any location restrictions
- Ensures safe connections are made to distant private networks
Characteristics of a Secure VPN
Without a robust set of security measures, a VPN that prioritizes user safety cannot demonstrate its worth. You should look into other risk-free alternatives if the supplier does not provide at least one of the characteristics listed below in their suite of available options.
- High Strength Encryption
Encryption is essential for VPNs because it renders your data unreadable and prevents it from being snooped on. These days, AES-256, ChaCha20, and quantum-resistant encryption are thought to be the most secure encryption ciphers available. DNS Leak Protection
Even if you are connected to a VPN, your Internet service provider (ISP) and malicious actors may still be able to record your activities if the VPN leaks your DNS. Due to this, it is very necessary for a VPN service to adopt extra safeguards for the prevention of DNS leaks.Kill Switch Function
In the event that your encrypted VPN connection drops, a kill switch is a safety mechanism that immediately disconnects your device from the internet. This helps to guarantee that your ISP, criminal actors, and websites that you visit do not have access to your IP address or other information about you.No-logs policy
In order for a VPN to protect your online privacy, it is necessary for it to not record everything that you do while you are connected. Only you will be aware of the activities that you engage in when you are onlineObfuscation
Deep Packet Inspection (DPI) is one example of a potent anti-VPN technology that is used by certain websites and agencies. VPNs may get over these bans with the use of obfuscation modes and servers, which also help disguise the fact that VPNs are being used.
Top 5 Best VPNs for Enterprise & Individual Use
There are several providers of VPNs, and the majority of them provide the same fundamental degree of encryption. These five service providers stand out from the others, however, since they are the most highly regarded by industry reviews and also give the most value for the money.
1. NordVPN
In the world of VPNs, NordVPN is among the most recognizable names in the business. It provides a substantial number of simultaneous connections, with six concurrent users across its network, although practically all other providers give five or less of these connections to their customers.
You will have access to the best security features when you sign up for a NordVPN membership, including as AES-256 encryption, the OpenVPN protocol, and Nord’s own unique NordLynx protocol. In addition, there are other features that are exclusive to NordVPN and cannot be found anywhere else, such as Meshnet, which transforms NordVPN into a worldwide version of a local area network (LAN).
NordVPN provides industry-leading digital security, making it the optimal choice for privacy-conscious users. Nevertheless, even inexperienced and casual VPN users may benefit from NordVPN’s outstanding range of additional features.
2. ProtonVPN
ProtonVPN has been rebranded as just Proton, and it now incorporates all of the other security measures that are part of the Proton package. This include such applications as ProtonMail, ProtonCalendar, ProtonDrive, and ProtonVPN. As a result, Proton is an excellent personal VPN service that can be used while working.
The VPN protocol used by Proton is called Stealth, and it includes one unique feature called obfuscation. Your data is encrypted, but it is also made to seem like ordinary traffic, which hides it from network filters, Internet service provider filters, and government filters. High levels of obfuscation are especially helpful in nations with strict regulations or extensive monitoring on the usage of VPNs.
Proton places a strong emphasis on protecting users’ personal information in the digital realm and offers a wide variety of services and products to that end. Therefore, you should think about using Proton if your line of work requires a higher level of discretion, such as sending sensitive information over the internet.
3. Surfshark
Surfshark is distinguished by its extensive collection of features pertaining to users’ privacy and security, as well as by its user-friendly interface, limitless simultaneous connections, and broad global network. Despite this, it is still quite a bit less expensive than the majority of its rivals.
In addition to the standard VPN features such as a kill switch and protection against DNS leaks, some of the more notable features of Surfshark include split-tunneling, camouflage mode (which conceals the fact that you are using a VPN), NoBorders mode (which enables you to use Surfshark in regions where VPNs are restricted), and multihop VPN connections. You’ll also get access to Surfshark’s CleanWeb technology, which helps you avoid being tricked by phishing websites by blocking advertisements and viruses.
Surfshark is for you if you are concerned that connecting to a VPN may get you into problems at public network domains, in the workplace, or in countries that do not permit the use of VPNs.
4. ExpressVPN
ExpressVPN excels at the one thing that any VPN should be able to perform extremely effectively, which is encryption. It offers a wide variety of secure VPN protocols in addition to the industry-standard 256-bit AES encryption that it employs as its foundation.
This service provider is a pioneer in the VPN industry. In addition to using already existing VPN protocols, it created its own proprietary protocol dubbed Lightway, which is characterized by both high levels of security and speed. This protocol works on just 2,000 lines of code, which is much fewer than other protocols, such as OpenVPN. As a direct result of this, it is both lightweight and delivers a streamlined experience for the user.
ExpressVPN provides flexible data security, making it an excellent choice in especially for those who travel often. It boasts robust privacy features, and the fact that it uses a lightweight proprietary VPN protocol makes it an excellent travel companion due to the fact that it operates quickly on the majority of mobile devices and desktops.
5. Atlas VPN
Even though Atlas VPN is a relatively new competitor in the market for VPNs, users are amazed by what it is capable of doing. With AES-256 encryption and a stringent privacy policy, this top-tier VPN provides all of the safety features of a top caliber service. In addition, we are given access to a plethora of other features, such as a free data breach monitor, numerous streaming platforms, a large number of simultaneous connections, IP addresses that change while we are surfing, and more.
The best part about this VPN is that it is not only affordable, but also has a plan that is free! The only limitation being that only 3 servers are available in the free plan out of hundreds worldwide. The Atlas VPN is an excellent choice for households. Basic identity protection may be offered to both children and their parents via the data breach monitor that is included at no additional cost with subscription plans.
Conclusion
Using a VPN is an easy method to secure your privacy while you are online, and it may also be used as a tool to get around undesired internet limitations. Since all service providers have similar benchmarks, and there will undoubtedly be situations in which it won’t make sense to utilize a VPN. Regardless, a VPN is without a doubt an ignored necessity, and it is highly recommended that you include it in your collection of personal security tools.