Applying Hacker Reasoning in Cybersecurity
Why Think Like a Hacker?
The methods hackers use to breach your network’s security are always evolving. There are always new hazards on the horizon, and it may be difficult for organizations to forecast what kind of compromise will occur. While no solution can ensure total security, developing a hacker’s outlook can help you to stay a few steps ahead of hidden dangers.
Cybercriminals use a variety of methods to gain access to networks. These may include the use of ransomware such as crypto lockers, leakware, scareware, and programs such as keyloggers, among others. Whatever approach is taken, the truth remains that fixing certain vulnerabilities demands a significant amount of time and effort on the part of cybersecurity specialists.
To fully comprehend how cybercriminals operate, it is vital to understand their regular process and techniques of moving via networks. This approach describes the procedures and human efforts necessary to penetrate an organization’s IT defenses.
Hacker Approaches
Hackers utilize a variety of approaches and tricks stretched out over a reasonable time frame to gain access to a network and create damage. You will be able to notice the process and put safeguards in place to avoid infiltration if you get familiar with these approaches.
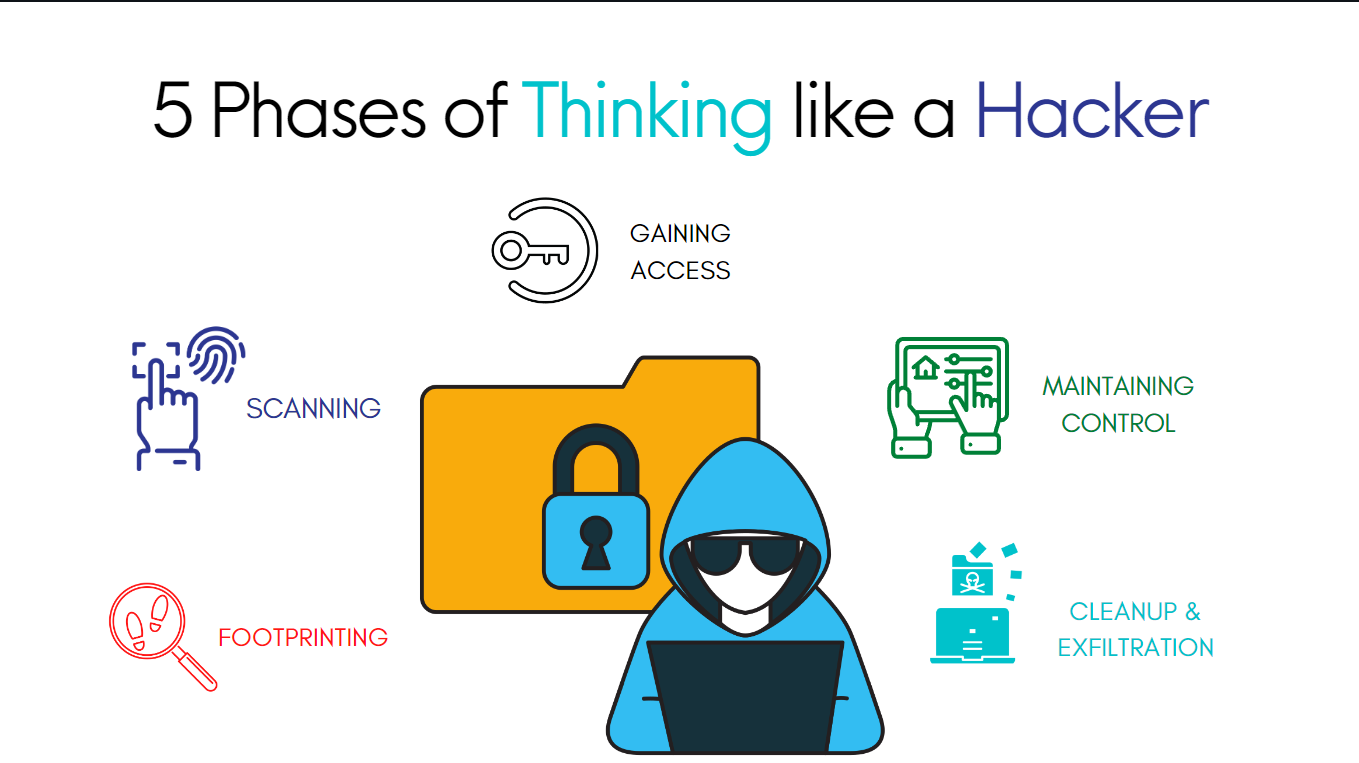
1. Footprinting
During “Footprinting,” a hacker gathers information about their target in preparation for an attack. At this point, hackers will try to do as much reconnaissance as possible about your firm and the target system, including contact information for personnel, the path taken by communications, critical system directories, and the like.
Before beginning an attack, hackers locate a weak spot and investigate potential entry points. The first victim might be any high-ranking employee or even a simple office worker. In order to launch an assault, the attackers need only get access to a single location. Email phishing attacks that specifically target a user’s email address are a typical tactic in this phase.
2. Scanning
Scanning is the procedure by which a hacker investigates the target system in search of vulnerable areas and other data. Port scanning is the most common technique used by hackers to locate potential entry points into a system or network. Scanning networks for hosts that are actively connected and scanning hosts for vulnerabilities are also part of this process.
Enumeration is the process by which an attacker learns about hosts on a network, including their identities, user groups, shared files, and other services. Obfuscating network details is a good approach to prevent enumeration if at all feasible. Since a hacker’s first line of attack is usually to do a DNS zone transfer in order to learn more about your network, it’s important to take precautions against this.
3. Gaining Access
Using the information gathered in the first two stages, the hacker now creates a plan for the target’s network. After enumerating and scanning the network, the hacker realizes they have a few entry points to choose from.
Accessing a single account is far less lucrative than taking over a whole network. To take over a whole network, a hacker has to be persistent, regularly assaulting new accounts and devices to gain access to critical information, plant seeds for future intrusions, and disseminate malicious software or hacking tools.
4. Maintaining Control
Once a hacker has gained access to your network, the next critical component of the assault is to stay undetected. Hackers may abuse the information to which they have access, which is why it is critical for enterprises to use distinct encryptions for various data segments. Breaches are often a greater issue than required because hackers have discovered a means to move from network to network, getting access to large quantities of data. Some malicious software goes undetected for months, enabling hackers to operate silently in the background.
5. Cleanup & Exfiltration
After a hacker has gained access to the target system and completed their desired actions, they will want to leave no trace of their intrusion. An essential part of the procedure, since the hacker must take care not to raise suspicion by drawing attention to their presence.
Cybercriminals will want to leave a back door open in the target system before they depart. In most cases, the “back door” refers to a hidden piece of software that may be used to circumvent the system’s regular safeguards. Besides gaining entry to the targeted system, the backdoor may be used to transform the compromised computer into a bot for distributed denial of service attacks or email spamming.
Conclusion
With the frequency and sophistication of cyberattacks rising every day, it is more important than ever to have many layers of protection in place. Having many safeguards and in place can lessen the likelihood that your network will be the next target of a cyberattack, but no solution will guarantee complete safety.
Outsourcing cybersecurity services and using sophisticated protection and monitoring technology can help ensure that your cloud security strategy is sound and that your customers’ data is safe, while allowing your own personnel to concentrate on other business matters.
Our team at Caplock Security is made up of devoted security professionals with years of experience in a variety of cybersecurity fields. Several of our clients have already used our assistance to improve their security standards, compliance requirements, and lower their risk. Our professionals can assist you in locating your security vulnerabilities and offer advice on how to fix them effectively.