5 Most Common Cloud Security Challenges & Solutions
Discover the essential steps to ensure a secure cloud infrastructure, from strategic planning to controlling third-party APIs and enhancing...
Picking the Ideal Cybersecurity Automation Tool in 2023
Explore the power of cybersecurity automation, an essential strategy to combat the increasing frequency and severity of data breaches,...
ChatGPT + Generative AI Vulnerabilities & Security Risks
Generative AI, powered by advanced language models like ChatGPT, has revolutionized our ability to generate human-like text, opening up...
7 Steps to NIST Risk Management Framework (RMF) Compliance
This article discusses the importance of implementing the 7 steps in NIST Risk Management Framework (RMF) for effective information...
How to Choose the Right Managed XDR for Your Organization
While XDR offers many benefits, it requires a lot of resources and expertise to manage effectively. Managed XDR...
Caplock Security Launches Managed Extended Detection & Response (XDR) Service
Caplock Security's Managed XDR service is positioned to meet the needs of organizations across various industries, including healthcare, government,...
Implementing Zero Trust Architecture (ZTA) in the Age of Remote Work
With the rapid shift to remote work, organizations face new cybersecurity challenges that require robust solutions. One such approach...
Top 10 AI Powered Cyberattacks to Watch for in 2023
This article discusses the increasing threat of AI hacking and AI-powered malware and provides real-life examples of their damaging...
Top 6 Must Know Cybersecurity Trends For 2023
Keeping up with the newest cybersecurity trends is the easiest method to ensure your organization's defensive plan is up...
5 Cybersecurity Strategies to Protect Critical Infrastructure
Utilizing technologies like cloud computing, advanced analytics, the open internet, and others, supply chains are now more digitized and...
Holiday Season Cybersecurity Threat Overview
During the holiday season, businesses of all sizes see a rise in cyber attacks between Christmas and New Year's....
Top 5 Must Track Cybersecurity KPIs & Metrics
With Cyberthreats always growing and becoming more difficult to identify, you must have methods in place to assess, record,...
Applying Hacker Reasoning in Cybersecurity
Developing the perspective of a hacker can enable organizations to stay one step ahead of potential threats by adequate...
Top 5 Tips to Improve Cloud Security
As the cyberthreat landscape has changed to incorporate cloud computing workloads, remote working, and third party communication, it is...
The 6 Essentials of Employee Security Awareness Training
The goal of cybersecurity awareness training & education for employees is to help them establish a sense of ownership...
5 Best VPNs for Cybersecurity
Why Use VPNs? A virtual private network (VPN) offers an additional layer of anonymity, permits access to foreign websites, and ...
Weekly Cyber Roundup (November 11, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
6 Tips for Hardware Security in 2022
Hardware security is crucial within an organization since the hardware layer is riddled with vulnerabilities that go unpatched for...
Weekly Cyber Roundup (November 4, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
5 Tips for Network Security in Healthcare
These 5 tips for network security in healthcare organizations are meant to be followed as a standard set of...
Weekly Cyber Roundup (October 28, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
HIPAA Software & Website Compliance Checklist
Cyberthreats to the healthcare industry have increased dramatically in the last decade along with the complexity of cyberattacks. The...
Weekly Cyber Roundup (October 21, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
HIPAA Violations in 2022 : Penalties, Fines and Consequences
There are several levels of penalties for breaching HIPAA laws depending on how much knowledge a covered organization has...
Weekly Cyber Roundup (October 14, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Cybersecurity Incident Response Guide For Healthcare Organizations
As cybersecurity incidents increase in the healthcare industry, it is more crucial than ever to develop an effective and...
Weekly Cyber Roundup (October 7, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
The Healthcare Industry’s Biggest Cybersecurity Vulnerabilities (2022)
Knowing the cybersecurity vulnerabilities that are faced by healthcare organizations is crucial, as it allow them to prepare and...
Weekly Cyber Roundup (September 30, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Top 5 Cybersecurity Tools for Healthcare Organizations
With the help of the five cybersecurity solutions covered, vulnerabilities of various kinds can be found and fixed, greatly decreasing...
Weekly Cyber Roundup (September 23, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
5 Security Strategies to Ensure Data Privacy in Healthcare
Organizations in the healthcare industry need to proactively secure their information through preventative manual procedures as well as software...
Weekly Cyber Roundup (September 16, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Protect Healthcare Data With These Cybersecurity Tips
These healthcare cybersecurity best practises are intended to keep up with the shifting threat landscape, addressing threats to endpoint...
The Importance of Cybersecurity in Healthcare
Cyberattacks are a particular worry for the healthcare industry because they can directly endanger patient safety and health, in...
Weekly Cyber Roundup (September 2, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Weekly Cyber Roundup (August 26, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
HIPAA Cybersecurity Compliance Essentials
Grasp the essentials of HIPPA cybersecurity and compliance requirements. Utilize our compliance checklist, certifications, and graphics in this article...
Weekly Cyber Roundup (August 19, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Spot Scams & Phishing with these 10 Email Security Essentials
With every organization interacting primarily with emails, it is necessary to ensure safe communication now more than ever. This...
Weekly Cyber Roundup (August 12, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
The Complete Ransomware Response Guide
This guide provides an in-depth guide for preparation, detection, analysis, containment, eradication, recovery, and post-incident activity phases of your...
Weekly Cyber Roundup (August 5, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Weekly Cyber Roundup (July 29, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Top 5 Ransomware Prevention Tips
A comprehensive, all-hands-on-deck strategy involving your entire organization is needed to combat ransomware. The five tips listed below can...
Weekly Cyber Roundup (July 22, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Weekly Cyber Roundup (July 15, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
The Impact of Ransomware on Businesses
It is a costly oversight to ignore the threat posed by ransomware, regardless of the size of your company....
What is Ransomware? – An Introduction
Ransomware can spread through networks that are not set up securely, harmful links and attachments in phishing emails, unintentionally...
Weekly Cyber Roundup (July 8, 2022)
Take a look at the most important cybersecurity news and key events that transpired this week.
Does your organization need CMMC certification?
The significance of CMMC accreditation is rising. It will soon be necessary in order to obtain Federal contracts. Your...
Weekly Cyber Roundup (July 1, 2022)
Take a look at the most important cyber news and events that transpired this week. Read about the most...
What is CMMC 2.0 Compliance? – A Beginner’s Guide
CMMC certifies officially that a business implements best practises in its cybersecurity operations and processes. The CMMC framework is...
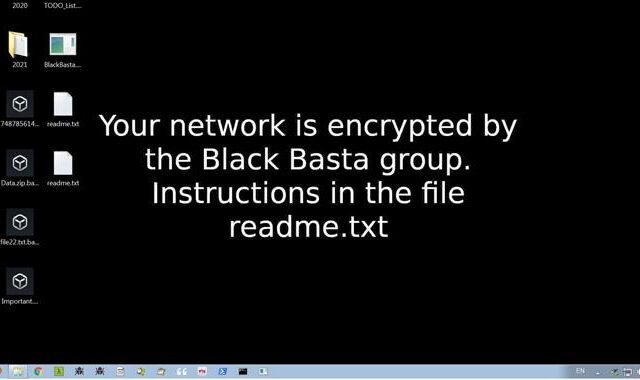
Cybersecurity Experts Warn of Emerging Threat of “Black Basta” Ransomware
Cybersecurity experts warn of emerging threat "Black Basta" ransomware. The Black Basta ransomware-as-a-service (RaaS) syndicate has amassed nearly 50...
CMMC Update: Pentagon Announces “Interim Rule”
By May 2023, the Department of Defense (DoD) intends to issue a "interim rule" that will incorporate the Cybersecurity...
Weekly Cyber Roundup (June 24, 2022)
Take a look at the most important cyber news and events that transpired this week. From the most recent...
Google Researchers Detail 5-Year-Old Apple Safari Vulnerability Exploited in the Wild
A security flaw in Apple Safari that was exploited in the wild earlier this year was originally fixed in...
Weekly Cyber Roundup (June 17, 2022)
Take a look at the most important cyber news and events that transpired this week. From the most recent...
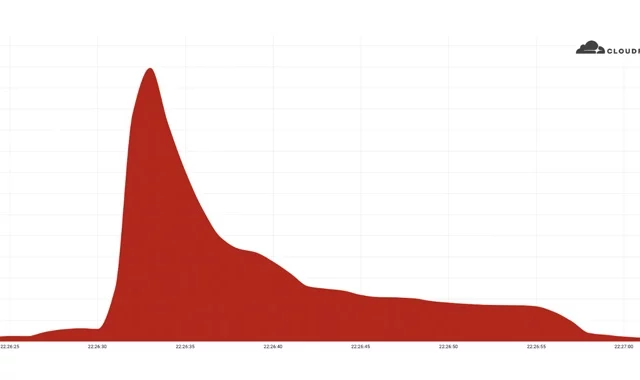
Cloudflare Saw Record-Breaking DDoS Attack Peaking at 26 Million Request Per Second
Cloudflare disclosed that it had acted to prevent a record-setting 26 million request per second (RPS) distributed denial-of-service (DDoS)...
Weekly Cyber Roundup (June 10, 2022)
WEEKLY CYBER BYTES 📅Mandiant and Lockbit have public display of affectionCISA advises on China's active exploit against major network devicesUK...
10 Most Prolific Banking Trojans Targeting Hundreds of Financial Apps with Over a Billion Users
10 of the most prolific mobile banking trojans have set their eyes on 639 financial applications that are available...
Weekly Cyber Roundup (June 3, 2022)
WEEKLY CYBER BYTES 📅Mandiant reports evil corp switches ransomware strain to allow victims to pay ransom and sidestep sanctionsMSFT vulnerability...
Weekly Cyber Roundup (May 27, 2022)
WEEKLY CYBER BITS 📅Twitter fined $150M for misrepresenting privacy practicesDuckDuckGo browser allows MSFT trackers - DuckDuckGo CEO responds INTERPOL arrest...
ExpressVPN Removes Servers in India After Refusing to Comply with Government Order
Virtual Private Network (VPN) provider ExpressVPN on Thursday announced that it's removing Indian-based VPN servers in response to a...
FBI Warns About Hackers Selling VPN Credentials for U.S. College Networks
"This exposure of sensitive credential and network access information, especially privileged user accounts, could lead to subsequent cyber attacks...
Web Trackers Caught Intercepting Online Forms Even Before Users Hit Submit
A new research published by academics from KU Leuven, Radboud University, and the University of Lausanne has revealed that...
New Bluetooth Hack Could Let Attackers Remotely Unlock Smart Locks and Cars
A novel Bluetooth relay attack can let cybercriminals more easily than ever remotely unlock and operate cars, break open residential smart...
Google Created ‘Open-Source Maintenance Crew’ to Help Secure Critical Projects
On Thursday, Google announced the creation of a new "Open Source Maintenance Crew" to focus on bolstering the security of...
GSA agrees to resolve Polaris small business concerns raised in pre-award protest
The General Services Administration has agreed to resolve a bid protest filed in late March over solicitations issued as...
White House Issues Two Quantum Directives Set To Bolster American Infrastructure
The Biden administration has announced two new directives that focus on incorporating quantum computing technology into the U.S. cybersecurity...
DOD expands vulnerability disclosure program to contracting base in pilot
DOD’s Cyber Crime Center, in partnership with HackerOne, just concluded a yearlong Defense Industrial Base-Vulnerability Disclosure Program (DIB-VDP) Pilot in...
U.S Cybersecurity Agency Lists 2021’s Top 15 Most Exploited Software Vulnerabilities
According to the "Top Routinely Exploited Vulnerabilities" report released by cybersecurity authorities from the Five Eyes nations - Log4Shell, ProxyShell, ProxyLogon, ZeroLogon,...
Cisco Releases Security Patches for TelePresence, RoomOS and Umbrella VA
Networking equipment maker Cisco has released security updates to address three high-severity vulnerabilities in its products that could be...
FBI, U.S. Treasury and CISA Warn of North Korean Hackers Targeting Blockchain Companies
U.S. government has issued a new warning about North Korean state-sponsored hackers targeting blockchain companies, including cryptocurrency exchanges, DeFi protocols, trading firms, venture...
Microsoft’s New Autopatch Feature to Help Businesses Keep Their Systems Up-to-Date
Last week, Microsoft announced that it intends to make a generally available feature called Autopatch as part of Windows Enterprise E3...
VMware Releases Critical Patches for New Vulnerabilities Affecting Multiple Products
VMware has released security updates to patch eight vulnerabilities spanning its products, some of which could be exploited to...
Google Issues Urgent Chrome Update to Patch Actively Exploited Zero-Day Vulnerability
Google Chrome users are urged to update to the latest version 99.0.4844.84 for Windows, Mac, and Linux to mitigate...
U.S. Government Warns Companies of Potential Russian Cyberattacks
The U.S. government has again warned of possible cyberattacks by Russia in retaliation for economic sanctions imposed by the West on...
FBI, CISA Warn of Russian Hackers Exploiting MFA and PrintNightmare Bug
FBI and CISA warn that Russian state-sponsored hackers are exploiting misconfigured multi-factor authentication (MFA) protocols and vulnerabilities in the Windows Print...
Google to acquire cybersecurity firm Mandiant for $5.4 billion
Google is officially buying cybersecurity company Mandiant in an all-cash deal approximately valued at $5.4 billion, the two technology...
U.S. Senate Passes Cybersecurity Bill to Strengthen Critical Infrastructure Security
The U.S. Senate unanimously passed the "Strengthening American Cybersecurity Act" on Tuesday in an attempt to bolster the cybersecurity...
Why companies are moving to a ‘zero trust’ model of cybersecurity
The zero-trust model of security, which takes the approach that no users or devices are to be trusted without...
VMware Issues Security Patches for High-Severity Flaws Affecting Multiple Products
The notorious TrickBot malware is targeting customers of 60 financial and technology companies, including cryptocurrency firms, primarily located in...
CISA, FBI, NSA Issue Advisory on Severe Increase in Ransomware Attacks
Cybersecurity authorities have published a joint advisory warning of an increase in sophisticated, high-impact ransomware attacks targeting critical infrastructure...
Microsoft Disables Internet Macros in Office Apps by Default to Block Malware Attacks
Microsoft disables internet-based VBA macros by default in Office applications to prevent phishing and malware attacks. "Bad actors send...
Biden Administration Forms Cybersecurity Review Board to Probe Failures
The Biden administration has formed a panel of senior administration officials and private-sector experts to investigate major national cybersecurity...
White House publishes final zero trust strategy for federal agencies
On Wednesday, The White House published a final version of its zero-trust architecture strategy, which is intended to substantially...
FBI Warns of Cybercriminals Using QR Codes to Steal Funds
The FBI issues warning for consumers using quick response/QR codes for contactless operations, stating that these codes can be...
Biden Signs Memo to Boost National Cybersecurity
President Biden has signed a National Security Memorandum requiring national security systems to implement network cybersecurity measures that are...
How The Internet Of Things Impacts Your Company’s Cybersecurity
Even the most advanced technologies are never bulletproof. According to a Juniper Research study, “the total number of IoT connections will reach...
Chair Rosenworcel Circulates New Data Breach Reporting Requirements
Jessica Rosenworcel, Chairwoman of the Federal Communications Commission (FCC) shared a Notice of Proposed Rulemaking (NPRM) to strengthen the...
NIST publishes updated draft guidance for engineers under Special Publication 800-160
NIST recently published updated draft guidance for engineers under Special Publication 800-160 “Engineering Trustworthy Secure Systems”. According to the...
Crypto Crime Trends for 2022
In a preview of their 2022 Crypto Crime Report, Chainalysis published a blog with the jarring finding that cryptocurrency-based...
DoD Publishes CMMC Assessment Guides for Level One and Level Two Assessments
The Department of Defense (DOD) published the Cybersecurity Maturity Model Certification assessment guides for level one and level two...
Feds Step Up Cybersecurity Support for State Governments
The Cybersecurity and Infrastructure Security Agency (CISA) is establishing a network of the fifty states to enhance cybersecurity efforts....
The Internal Revenue Service (IRS) Is Making Progress On Securing Its Systems And Data
The Treasury Inspector General for Tax Administration released a 92-page report outlining that while the Internal Revenue Service (IRS)...
NIH’s core security functions remain deficient
The Government Accountability Office (GAO) issued a report on Tuesday stating that the National Institute of Health’s (NIH) core...
DISA’s new HaCC office reflects hybrid cloud reality for DOD
The Defense Information Systems Agency (DISA) has established a new office that acknowledges the benefits of hybrid cloud solutions...
White House Readies Plan to Boost Cybersecurity of Water Supply
Concerns around securing the U.S. water supply are taking on a new sense of urgency due to growing threats...
DHS Announces New Cybersecurity Requirements for Surface Transportation Owners and Operators
The Department of Homeland Security’s (DHS) Transportation Security Administration (TSA) announced two new security directives for measures to strengthen...
Hacker, Journalist Among CISA Directors’ 23 New Cybersecurity Advisors
Following the establishment of the Cybersecurity and Infrastructure Security Agency (CISA) advisory committee in June 2021, the agency director,...
Up to 1.2 million GoDaddy customers’ data exposed in breach
1.2 million customers of GoDaddy, a popular web host and domain registrar, may have had their data accessed by...