What is CMMC 2.0 Compliance? – A Beginner’s Guide
What is CMMC compliance?
The United States Department of Defense (DoD) established the Cybersecurity Maturity Model Certification (CMMC) program to assess defense contractors’ cybersecurity skills, readiness, and competence. The framework is a combination of procedures, guidelines, and inputs from existing cybersecurity standards like the National Institute of Standards and Technology (NIST) , Federal Acquisition Regulation (FAR), and Defense Federal Acquisition Regulation Supplement (DFARS) at a high level.
The CMMC program’s main purpose is to increase the trustworthiness and security of Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) maintained by Federal contractors. Cyber security guidelines for enterprises in the defense industrial base are part of the CMMC program. CMMC gives the Department assurance that contractors and subcontractors are following DoD cybersecurity requirements by embedding cybersecurity standards into procurement programs.
Malicious actors and non-state groups are increasingly targeting the Defense Industrial Base (DIB) with increasingly complicated cyberattacks. The DoD’s main objective is to dynamically improve DIB cybersecurity to address these emerging threats, as well as to safeguard the information that supports and enables our fighting forces. CMMC is an important part of the Department’s large-scale DIB cybersecurity initiative.
Below is a brief timeline of CMMC related events:
- On January 31, 2020, the CMMC program was unveiled
- DoD began issuing a limited number of requests for information with CMMC standards in September 2020
- It is predicted that by 2026, CMMC will be a prerequisite of all new DoD requests for proposals
What is the purpose of implementing CMMC?
Before the CMMC, all contractors handling sensitive government data and information (CUI) were required to follow the standards outlined in DFARS Clause 252.204-7012, Safeguarding Covered Defense Information and Cyber Incident Reporting. The criteria demanded adherence to NIST 800-171 cybersecurity procedures, which the Defense Industrial Base (DIB) would self-certify as being met.
The prior self-attestation strategy, however, was deemed insufficient to secure the defense supply chain from potential IP theft and cyber intrusions. Malicious cyber activity is predicted to cost $57 billion per year in economic costs, and cyber breaches could potentially endanger the US economy and national security.
In recent years, attackers have shown a rapid expansion in complexity and operational security skills. Significant and persistent attacks on defense industries’ networks and systems are emerging. The CMMC was established to boost the Defense Industrial Base’s cybersecurity capabilities (DIB). It guarantees that contractors protecting sensitive information on behalf of the government follow industry standards.
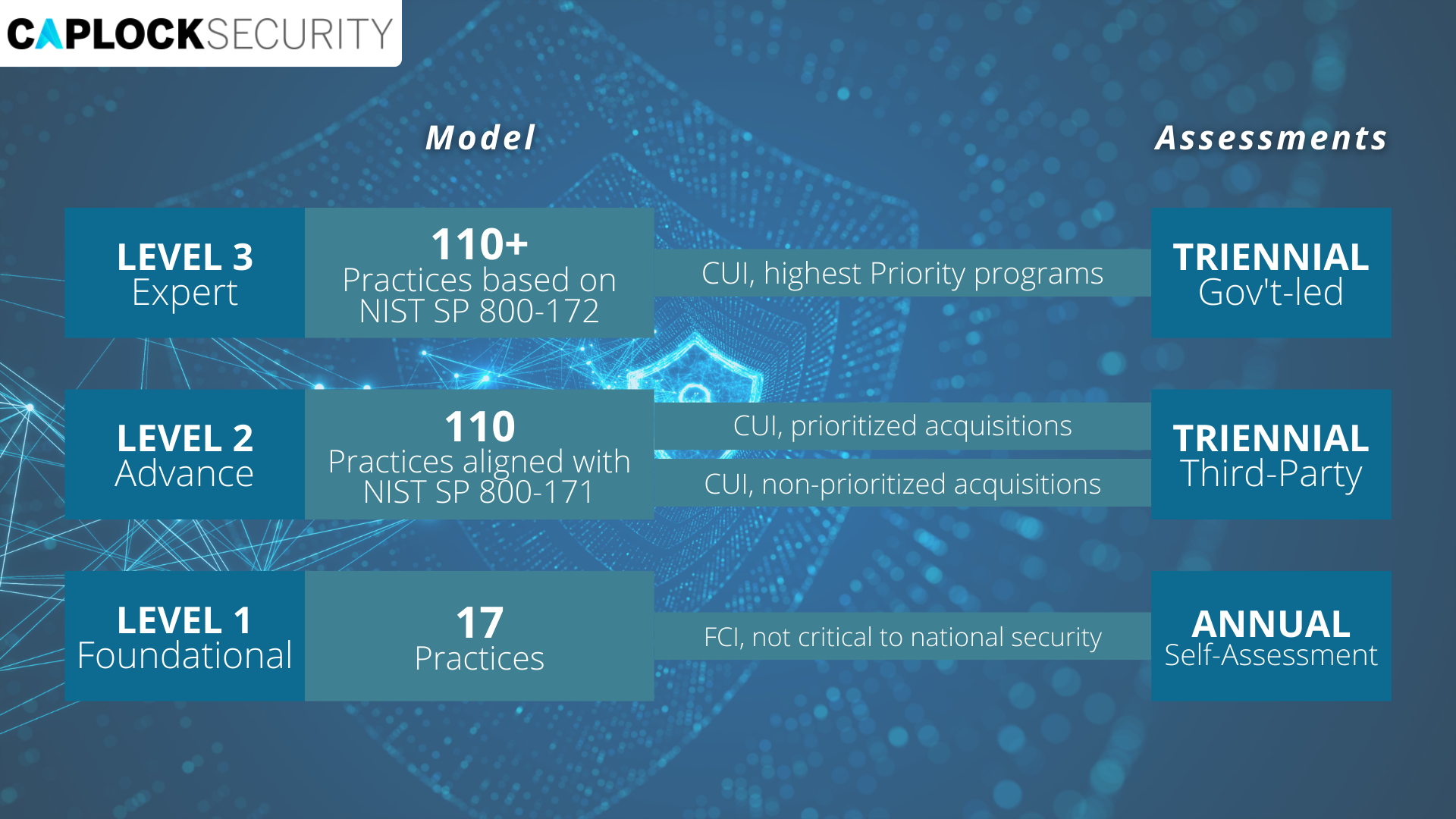
What are the 3 different levels of CMMC 2.0?
The CMMC framework consists of the security requirements from NIST 800-171 Rev 2, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, and a subset of the requirements from NIST SP 800-172, Enhanced Security Requirements for Protecting Controlled Unclassified Information: A Supplement to NIST Special Publication 800-171. The model framework organizes these practices into a set of domains, which map directly to the NIST 800-171 Rev 2 families. There are three levels within CMMC- Level 1, Level 2, and Level 3.
CMMC levels and associated sets of practices are cumulative across domains. To be more specific, in order to reach a certain CMMC level, an organization must also demonstrate achievement of the lower levels that came before it. If an organization does not attain its goal level, it will be certified at the highest level for which all applicable procedures have been met.
The three levels are scaled and built on the requirements of the previous levels. Each level involves compliance with lower-level regulations as well as the implementation of additional processes to apply specified cybersecurity-based procedures.
The three levels of CMMC are:
- Level 1
Includes the FAR Clause 52.204-21’s fundamental safeguarding standards for FCI. Only activities that adhere to the basic safeguarding standards outlined in 48 CFR 52.204-21, usually referred to as the FAR Clause [3], are included in Level 1, which focuses on the protection of FCI. - Level 2
Covers the security standards for CUI as outlined in NIST SP 800-171 Rev 2 [3, 4, 5], as well as the DFARS Clause 252.204-7012 [3, 4, 5]. The 110 security standards listed in NIST SP 800-171 Rev 2 [4] are covered by CMMC Level 2, focusing on the protection of CUI. - Level 3
Measures for minimizing the risk of Advanced Persistent Threats (APTs) Information on Level 3 will be available at a later date and will include a subset of the NIST SP 800-172 [6] security standards.
Contractors and vendors must meet the specifications for procedures and processes associated with each certification level across these 14 domains that align with the families specified in NIST SP 800-171 in order to reach the targeted level.
• Access Control (AC) • Awareness & Training (AT) • Audit & Accountability (AU) • Configuration Management (CM) • Identification & Authentication (IA) • Incident Response (IR) • Maintenance (MA) | • Media Protection (MP) • Personnel Security (PS) • Physical Protection (PE) • Risk Assessment (RA) • Security Assessment (CA) • System and Communications Protection (SC) • System and Information Integrity (SI) |
Conclusion
CMMC independently certifies that a company follows best practices in cybersecurity processes and operations. There are three levels to the CMMC framework. Starting with fundamental safeguarding of FCI at Level 1, advancing to wide protection of CUI at Level 2, and finally minimizing the risk of Advanced Persistent Threats (APTs) at Level 3. The CMMC framework is reinforced by a certification scheme that verifies the practices’ implementation.
The CMMC framework was developed in partnership with a community of DoD stakeholders, UARCs, FFRDCs, and the DIB sector to fulfill the DoD’s demands for unclassified information protection during the purchase and maintenance of products and services from the DIB.
Since CMMC is meant to grow with an organization’s maturity level, it may be used to benchmark and improve a company’s cybersecurity capabilities. These enhancements make information more secure while also improving network and system best practices. Organizations gain from upgrading their systems and processes since the repercussions of a cybersecurity breach can be severe.
This concept is one of several initiatives being pursued by the DoD and industry to improve the security of the DIB sector. These activities are critical in laying the groundwork for future DoD acquisitions by establishing cybersecurity as a basis.
If your organization functions as a defense contractor with the DOD, and deals with CUI and FCI, you must ensure that the CMMC level data protection requirements are met. Caplock Security offers a broad range of services and solutions to help organizations facilitate change, achieve their vision and optimize performance and productivity.