CMMC Update: Pentagon Announces “Interim Rule”
Pentagon to Publish Updated CMMC Implementation Timeline
According to Stacy Bostjanick, the Pentagon’s director of CMMC policy, the Department of Defense (DoD) plans to release an “interim rule” to implement the Cybersecurity Maturity Model Certification (CMMC) requirements in defense contracts by May 2023.
Currently, the CMMC requirements are undergoing the Code of Federal Regulations (CFR) and the Defense Federal Acquisition Regulation Supplement (DFARS) federal rulemaking process, which is required prior to full implementation.
If granted an interim rule decision, CMMC requirements may start to appear in DoD contracts as early as July 2023, 60 days after the rule’s publication.
However, at an event hosted by the Potomac Officers Club, Bostjanick noted that an interim rule publication is “not guaranteed.” Bostjanick stated, [the Pentagon] could come back and say, ‘No, we don’t see the urgency of this meeting to be an interim rule and [the DoD] will not be allowed to implement until [the DoD goes] through final rule.’
Bostjanick noted that upon the rule’s publication, the DoD will take a phased approach to ensure the entire CMMC ecosystem will be capable of handling contractor certification requests. The CMMC ecosystem comprises of cybersecurity assessor and instructor certification organizations, assessors, and the Defense Industrial Base Cybersecurity Assessment Center, among others.
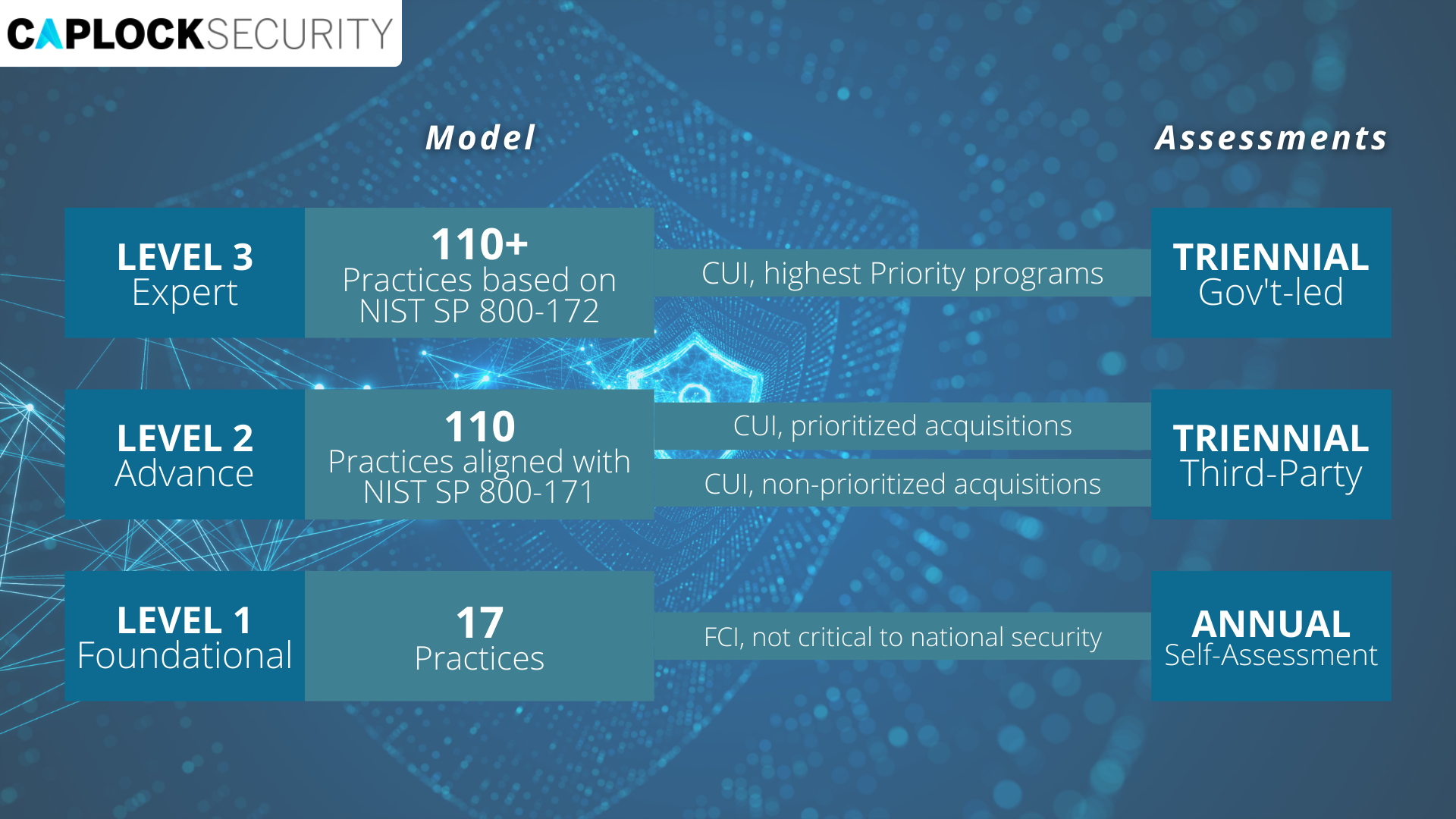
CUI Priority Types and CMMC Levels
Bostjanick also provided insights into prioritized and non-prioritized Controlled Unclassified Information (CUI) and how that will impact CMMC levels and assessments.
Currently, there are no clear definitions of what exactly is prioritized and non-prioritized CUI, but the rough definitions indicate that non-prioritized CUI involves information that is low risk and would not cause harm if released (e.g., military uniform material). A rough definition of prioritized CUI is any information that would cause harm, loss of capabilities, or advantages if adversaries had access to it.
Bostjanick noted that future contracts will indicate whether the procurement involves prioritized or non-prioritized CUI, or Level 3 CUI. For the companies that only handle non-prioritized CUI, Bosjanick noted that they could “do a self-assessment, an annual affirmation that they meet the requirements of NIST 800-171 to handle non-prioritized CUI.” However, if Level 3 CUI is required, then a CMMC Level 3 (Expert) assessment must be conducted by the Defense Industrial Base Cybersecurity Assessment Center.
“Anybody who handles CUI and bids on more than one contract will most likely have to have a third-party assessment, because it’s only ever going to take one contract that you bid on that requires that third-party assessment to drive you to that level” – Stacy Bostjanick
As of June 2022, this new update on the interim rule means defense contractors have less than a year to become CMMC compliant.
However, your defense company may or may not already be ahead of the race. Since 2017, contractors have been required to meet the 110 security controls of NIST SP 800-171, which the new CMMC Level 2 (Advanced) requirements will mirror. The major difference being that both CMMC Level 2 and Level 3 require third-party assessments every three years.
As the CMMC rulemaking process continues to unfold, government contractors should continue to monitor and enhance their cybersecurity posture in preparation for CMMC 2.0. For companies that have yet to start their CMMC journey, the window is closing. To keep up with the speed of the Pentagon, businesses that deal with contract work need to start their CMMC Certification process now.
At Caplock Security, we can help contractors prepare for CMMC compliance or help determine the most effective path forward for developing and maintaining cybersecurity processes and equipped personnel.