HIPAA Software & Website Compliance Checklist
Cyberthreats to the healthcare industry have increased dramatically in the last decade along with the complexity of cyberattacks. The threat of malicious intrusions escalates with each improvement brought about by automation, interoperability, and data analytics. Cyberattacks are especially a significant concern for the healthcare sector since they may directly jeopardize patient safety and health, as well as system and data security.
Importance of HIPAA Compliance
The Health Insurance Portability and Accessibility Act (HIPAA) is a regulation that aims to protect patient health information in the US. The security controls, methods, and procedures defined in the HIPAA regulation must be implemented by certain organizations that have access to protected health information (PHI). Sensitive patient health information, including treatment specifics, test results, personal identification information, and demographic data, is protected by HIPAA from being shared without the patient’s permission.
- As hospitals, clinics, and small medical practices are now compelled to bring their systems up to speed with modern technology, the need for designing HIPAA-compliant software is at an all-time high.
- When you include in the tremendous increase in smart healthcare services, it’s no surprise that healthcare software developers are in great demand.
- However, creating or purchasing healthcare software is significantly more difficult than developing general software solutions.
To fulfil HIPAA’s stringent compliance standards, healthcare software must be custom-designed. Generic software does not fulfil HIPAA’s stringent security and privacy requirements. Healthcare software must be carefully developed to send, receive, and retain electronically protected health information (ePHI) while minimizing the risk of data breaches or lost records.
HIPAA Penalties
There are multiple tiers of penalties for violating HIPAA laws, depending on how much information a covered business has of the violation. Ignorance of the HIPAA regulations is not a valid justification for violating them. Each covered entity is responsible for ensuring that the HIPAA standards are understood and followed. When a covered entity is determined to have deliberately violated a HIPAA law, the most severe penalties are levied.
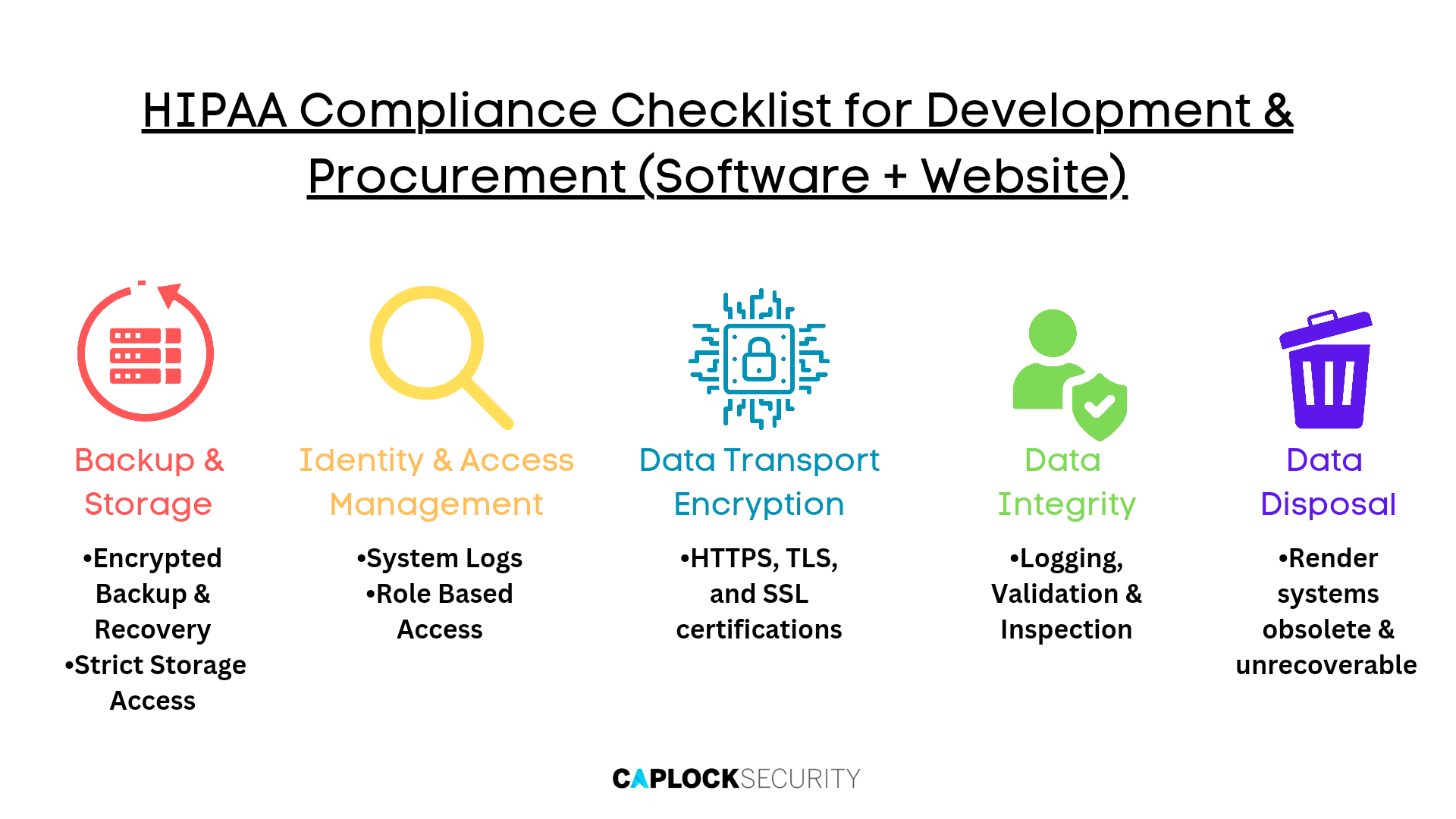
HIPAA Compliance Checklist for Development & Procurement (Software + Website)
The Security Rule of HIPAA outlines the standards for safe electronic transfer and storage of sensitive patient data. While transferring patient data online has improved healthcare administration efficiency and mobility, it has also raised security risks for medical staff. The HIPAA Omnibus Rule, a series of legislative modifications that updates the original Act to take into account new technology, must be complied with by healthcare organizations. The following elements listed below must be present for healthcare platforms to be completely HIPAA compliant.
Backup & Storage
When dealing with sensitive PHI, it is critical to ensure that information is only accessed by authorized employees. This includes any data saved in your software system, such as databases, backups, and logs. It may be kept in places outside your control, such as a server shared with other consumers on the same hosting provider. If this server is hacked in any manner, the data must remain encrypted and unavailable.
- To prevent attackers from deciphering data breaches, all data must be encrypted before transmission
- Ensuring HTTPS and certificates are used to encrypt transmission channels
- Data encryption should also be used at the storage site to protect it from database intrusions
- Implement software that can recover and restore lost data from system failures
- Backup data should be encrypted as soon as possible
Most hosting companies provide backup and recovery services to ensure that data is not lost in the event of an accident or breach. Although this is a convenient option, data should be backed up, securely kept, and only accessible to authorized personnel.
Identity and Access Management
Identity and access management are critical for maintaining HIPAA compliance. Passwords and user IDs for institutional data must be kept as secure as possible and never shared among staff. HIPAA has extremely rigorous standards concerning the degree of security that must be maintained to preserve the privacy and security of user data.
- System logs are an essential component of HIPAA compliance. To monitor all login attempts and modifications to PHI, the system should generate access logs and event logs.
- Two Factor Authentication (2FA), which uses two kinds of authentication to authenticate an individual’s identity, should be used to guarantee that only authorized users have access to sensitive data and information.
- Single-Sign On allows users to safely check in once and then access a network of apps and websites without having to sign in again during a single session. This is important for healthcare professionals who need to rapidly and effectively acquire access to user data across an ecosystem of applications and sites without jeopardizing the protection of institutional data.
- Attribute Based Access Control is another method for tackling issues with user role management. This enables dynamic and contextual access to numerous places, applications, and other resources based on access control rules that are based on characteristics rather than persons and activities. Individual traits are much more adaptable, particularly when it comes to altering structural regulations over time. This is particularly useful in conventional role-based authorization when responsibilities overlap.
Data Transport Encryption
Before being transferred, any ePHI (electronic Protected Health Information) must be encrypted. HIPAA-compliant software encrypts sensitive health data during transmission, and the first step is to protect it using SSL and HTTPS protocols. According to the HIPAA compliant hosting checklist, your public or private cloud provider should enable you to configure your SSL to guarantee robust encryption mechanisms. The former safeguards sites that gather or display health information, as well as login pages. There should be no non-secure variations of these pages.
- It is advised to ensure that the HTTPS protocol is correctly configured and that there are no expired or insecure TLS versions
- Passwords may be communicated and saved using hash values. This, together with safe complicated passwords, may help to avoid compromising situations
Data Integrity
It is critical to guarantee that the information you gather, store, and send is not corrupted or changed in any manner, whether deliberately or unintentionally. The first step is to ensure that your system is capable of detecting and reporting any illegal data manipulation, even if just a single piece has changed.
This is accomplished in website creation by digitally signing and then validating every piece of data saved or communicated in the system using tools such as PGP, SSL, and others. The whole system must then be developed and implemented in such a manner that illegal access to the data is prevented.
Regular backup, encryption, access authorization with suitable user roles and rights, and physical access limitation to the infrastructure are all important factors in making your medical software HIPAA-compliant.
Data Disposal
Data that has been backed up and archived must expire and be permanently disposed of. This is especially applicable for all decryption keys. It must be anticipated that backups or copies of the data will be made at each site where it is transferred. To guarantee healthcare data security and HIPAA compliance, data must be disposed of once a server is no longer in use.

Conclusion
HIPAA’s main objective is to safeguard the PHI given to covered companies and their business partners. Organizations are required under the HIPAA Privacy and Security Rules to manage and track PHI access and safeguard it from unauthorized access.
Caplock Security offers a variety of solutions that help healthcare providers and other organizations achieve compliance with HIPAA and other regulations. Bring the best out of your organization by relying on our cybersecurity professionals for tasks such as:
- Identifying unknown flaws or vulnerabilities that can result in a breach or disclosure.
- Validating, understanding, and preparing for known risks to your organization.
- Updating and maintaining regulatory or compliance controls.
- Providing clear, action-oriented recommendations designed to provide time-to-value in improving your security posture.
Avoid the costly mistake of neglecting your organization’s cybersecurity aspect. Caplock Security gives you all the tools you need to streamline your security deployment without sacrificing performance, allowing for a unified strategy for efficient operations and getting you ready to scale for corporate expansion. Reach out to see what we can do for you today.