5 Cybersecurity Strategies to Protect Critical Infrastructure
The Risk to Critical Infrastructure
Organizations must adopt a deeper, more comprehensive perspective in how they build and manage cybersecurity and cyber resilience solutions as a consequence of the digitized approach to critical infrastructure.
- Utilizing technologies like cloud computing, advanced analytics, the open internet, and others, supply chains are now more digitized and diversified than ever.
- This has broadened the attack surface and uncovered new vulnerabilities where vital infrastructure may be exposed to extreme physical occurrences, breaches, and other circumstances that may result in downtime.
Nature and physical assault are no longer the sole dangers to infrastructure. Critical industries are becoming more and more reliant on wireless and linked technologies and as a result, the risks they encounter have changed as well. Network resilience and security are critical to guaranteeing continuous connectivity. Constant attention and checks can help to secure infrastructure, but they are not always adequate.
This article provides an overview of the five important strategies to help organizations protect themselves against cyberattacks against their critical infrastructure.
How to Protect Critical Infrastructure from Cyberattacks?
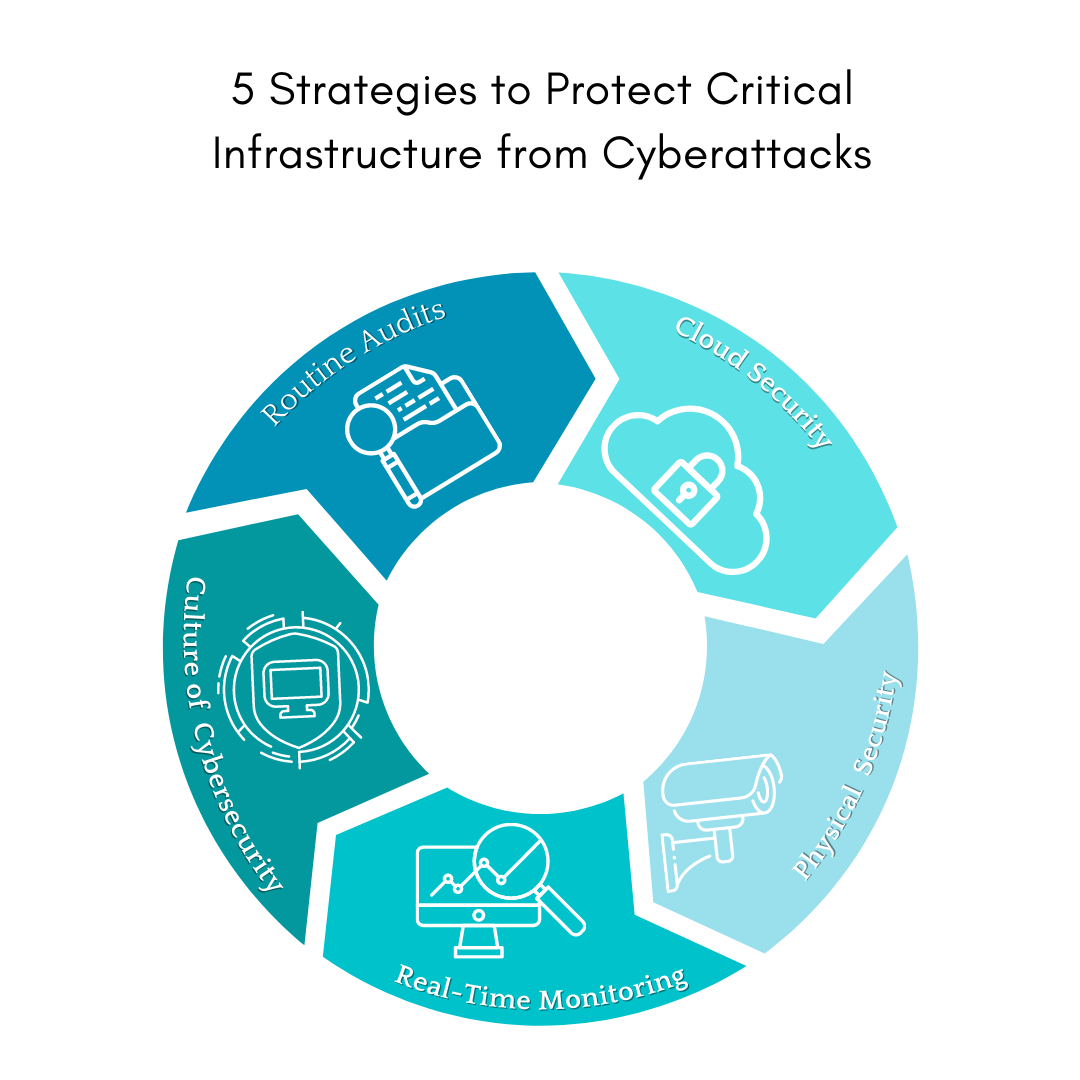
Here are five cybersecurity strategies to help you eliminate security vulnerabilities, obtain visibility into your daily operations, and ensure complete protection from internal and external threats.
1. Ensuring Cloud Security
Companies may take numerous steps to secure cloud security and protect critical infrastructure, such as
- Choose a cloud service provider with a proven track record of security and compliance.
- Use identity and access management (IAM) control systems to allow access to only authorized users and limit access to sensitive data.
- Encrypt data at rest and in transit, including data saved in the cloud and data transferred across networks.
- To guard against cyber attacks, use security solutions such as firewalls, intrusion detection and prevention systems, and vulnerability scanners.
The ability to control all cloud resources from a single unified plane is a crucial step toward risk reduction for critical infrastructure. A consistent cloud security and networking policy throughout the enterprise is ensured by having a single operational hub for all clouds, allowing IT teams to identify, defend, detect, respond, and recover with increased speed, confidence, and intelligence.
2. Strict Physical Security
Servers are a critical component of a company’s infrastructure, and any manipulation or damage to this gear may result in massive losses. Servers should thus be safeguarded by being placed on racks in dedicated server rooms. To avoid tampering, these ‘server cabinets’ should have lockable doors, and the front bezels of individual servers should likewise be protected with a lock. The temperature and atmosphere of the room must be properly managed to avoid server damage from overheating or dampness.
Locked doors, on-site security personnel, tight identification verification, and CCTV cameras should be used to safeguard the premises. It is critical to monitor IT server rooms and staff devices. Access to important hardware should be controlled, and physical access privileges should be managed with the same zeal as software access privileges. Individual, team, department, and organizational permissions may be easily adjusted using cloud-based access control systems.
3. Use real-time monitoring
Real-time hardware monitoring guarantees proper security and prevents illegal acts, which is particularly important in organizations with remote employees. Cloud-based real-time monitoring solutions alert security professionals in the event of a hardware compromise and enable rapid incident response. Implement visual verification methods, activity reporting, and remote access to physical equipment whenever practical. This will assist in reducing reaction times in the event of a security breach.
Gradually, start planning to utilize integrated platforms and IoT automation to get a complete picture of your company’s hardware security posture. This data may be analyzed using artificial intelligence-powered analytics to allow the proactive adoption of business security measures as needed.
4. Foster a Culture of Cybersecurity
Cyber security awareness is primarily a mental condition. Your behavior and ideas while performing tasks define who you are. It is your approach toward maintaining security, protecting your personal information, and coping with risk in your professional and private life. Furthermore, it is a talent that can be honed and perfected with practice.
Employee cyber security education is to instill in them a sense of responsibility for their own safety in the face of cyber threats, as opposed to a passive acceptance of risk. Smaller businesses may lack access to specialized security professionals, but any interested employee with the required resources can attend security training classes.
5. Conduct Routine Audits
Auditing your present hardware security and cybersecurity postures on a regular basis is always a smart idea. Set up audits to identify and manage operational hazards. Enhance your audits by performing frequent vulnerability testing and system monitoring. This will assist in safeguarding your company from emerging dangers.
Audits of hardware security must be rigorous, time-consuming, intrusive, and, in some cases, harmful. If the cause for its appearance is unknown, electrically inspect the inputs and outputs of any questionable modules after consulting with the manufacturer and your in-house hardware specialists. Compare the architecture of sensitive systems in your business to reference pictures certified by the original manufacturer.
Conclusion
To avoid cyberattacks on critical infrastructure, organizations need to follow the strategies listed above as well as ensure data compliance regulations within their respective regions.
Outsourcing cybersecurity services and using contemporary protection and monitoring technology can help ensure that your healthcare security strategy is sound and that your customers’ data is safe, while allowing your own employees to concentrate on other business matters.
Our team at Caplock Security consists of security experts with years of expertise in a range of cybersecurity disciplines. Several of our clients have already used our services to enhance their security standards, meet regulatory requirements, and reduce risk. Our expertise can help you in identifying security flaws and provide guidance on how to properly address them.